encryptCTF2019 Pwn Write-ups
Our team (hackstreetboys) decided to participate @ encryptCTF 2019 hosted by Abs0lut3Pwn4g3. Luckily, we finished 52nd place out of 696 participants.
For this multi-part write-up, I will discuss how I finished all challenges in pwn category.
 |
|---|
| First pwn board wipe of the year. hsb represent! :) |
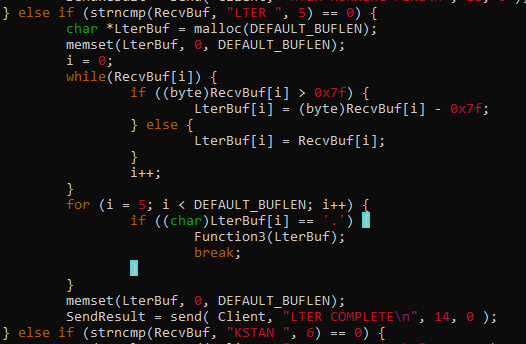
- Pwn0 (Basic buffer overflow exploit)
- Pwn1 (Basic buffer overflow exploit)
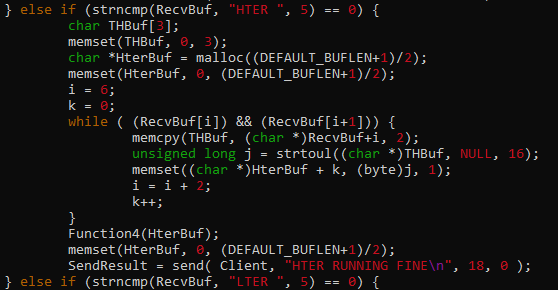
- Pwn2 (gets()+ system() ROP chain)
- Pwn3 ( Libc leak + ROP chain)
- Pwn4 ( Format string exploit )
-
— ar33zy
hackstreetboys aka [hsb] is a CTF team from the Philippines.
Please do like our Facebook Page and Follow us on Twitter, Medium, and GitHub.