Exploiting vulnserver.exe — Intro to Windows Exploitation
In this multipart write-up, I will feature vulnserver.exe— a binary that is designed to be exploited. I used this binary to have a quick introduction on Windows exploitation development, since I am only familiar with exploiting Linux binaries.
For the test environment, I used Windows 7 x86 VM with the following tools:
And of course, vulnserver.exe as our victim binary.
By default, vulnserver listens on port 9999.

The source code is also included upon downloading the compressed file, which helped me a lot in identifying the vulnerabilities of the program.
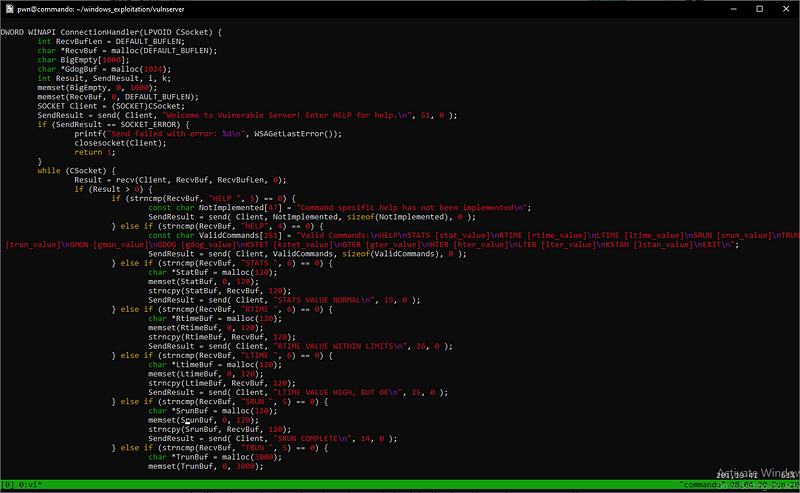
Upon checking the source code, I have identified 6 vulnerable commands (out of 14) that could lead to stack-based buffer overflow. The vulnerable commands are as follows:
- TRUN
- GMON
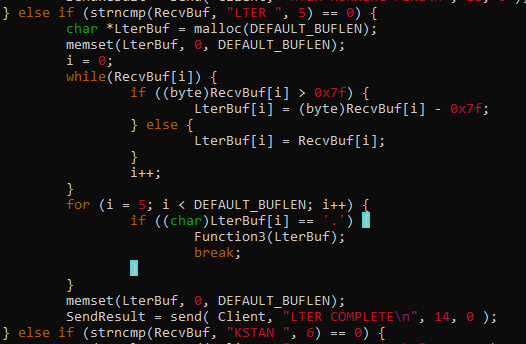
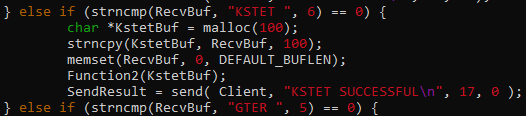
- KSTET
- GTER
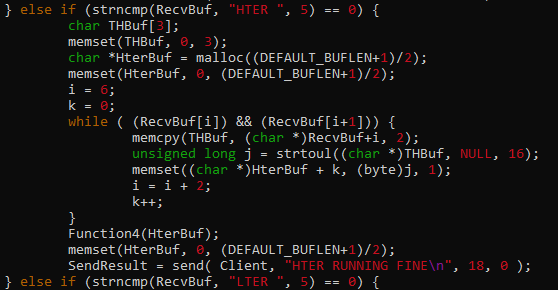
- HTER
- LTER
All these commands have a common culprit — strcpy()
The
strcpybuilt-in function does not check buffer lengths and may very well overwrite memory zone contiguous to the intended destination.
Which explains why all these commands are vulnerable to buffer overflow. The exploit for each command will be discussed separately.
- TRUN ( jmp esp )
- GMON ( SEH )
- KSTET ( jmp esp + egghunter )
- GTER ( jmp esp + egghunter )
- HTER ( str2hex payload + jmp esp )
- LTER ( jmp esp + badchars bypass )
To mitigate this vulnerability, alternative functions like strncpy() should be used. There are a lot of resources online that can be used as a reference for secure coding. Below are some of the examples:
- https://rules.sonarsource.com/c/type/Vulnerability/RSPEC-5782
- https://security.web.cern.ch/recommendations/en/codetools/c.shtml
- https://medium.com/@int0x33/day-49-common-c-code-vulnerabilities-and-mitigations-7eded437ca4a
— ar33zy