HTB Writeup - Traverxec

Traverxec is one of the beginner friendly boxes in HTB. This machine is hosting a webserver vulnerable to remote code execution, exposing a backup SSH private key for user pivot, and allowing a non-privileged user invoke journalctl as root leading to machine pwn.
Recon
A quick masscan + nmap scan gives us the following info:

It seems that the entry point for this machine is limited to 2 ports, via HTTP and via SSH. Credentials are needed for SSH access so let’s proceed with checking up the web server. Take note that the web server is running nostromo 1.9.6.
Nostromo Webserver
Upon checking up the web server, it hosts a static page showing David White's portfolio.

Since this is a easy box, one of the checklists is to search for nostromo 1.9.6 on Exploit DB. Searchsploit can be used to query for existing exploit scripts.

There is an existing python script that can be used to do an RCE to the webserver. This script can be pulled using -m parameter.
The script can be used as python 47837.py <Target_IP> <Target_Port> <Command>.
A quick check using id shows that the current user is www-data. There is also a netcat binary that has -e option enabled, this command can be used to do a reverse shell for easier access on the machine.

PrivEsc to David
A quick check on /etc/passwd/ shows that there is a user named david in this machine (david - David White the web developer lol).

Sadly, www-data does not have enough privileges to access david's home directory. Back to the drawing board.

Backtracking to nostromo web server. The config file gives us the following info:

There are notable infomation in this conf file:
# HOMEDIRS [OPTIONAL]
homedirs /home
homedirs_public public_www
According to nhttpd documentation, homedirs option serves the home directories of the machines’ users. This directory can be accessed by entering ~<user> in the URL.

Next, homedirs_public restricts the access within the home directory into a single sub directory. This means that our access is limited to public_www directory.
We can check the contents of /home/david/public_www/ via shell.
Upon checking, there is a tgz file (backup-ssh-identity-files.tgz) inside /home/david/public_www/protected-file-area/. This file can be extracted using netcat.

The tgz file contains david’s backup SSH keys.

The private key needs a passphrase, this can be cracked using ssh2john.

The passphrase is hunter. The private key can now be used to login via SSH as david.
Note: Do not forget to change the file permission of id_rsa to 400/600.

PrivEsc to Root
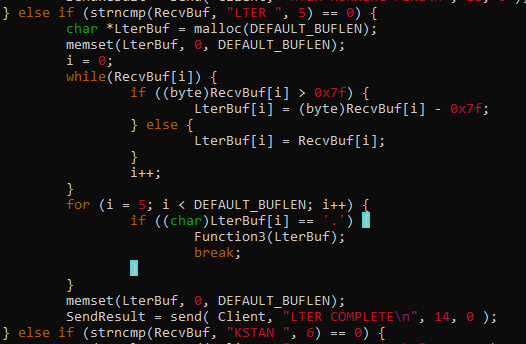
A quick check on the files inside the home directory shows that there is a script worth investigating.

This line in the script can be abused.
/usr/bin/sudo /usr/bin/journalctl -n5 -unostromo.service | /bin/cat
According to GTFObins, journalctl invokes a pager. Pager tools can be abused via shell escape.

Since journalctl can be executed as root, we can use this technique to escalate privileges.

Executing this command did not invoke a pager, and that is because of -n parameter. According to journalctl man page,
-n, --lines=
Show the most recent journal events and limit the number of events shown. If --follow is used, this option is implied. The argument is a positive integer or
"all" to disable line limiting. The default value is 10 if no argument is given.
The trick we can use is minimizing the terminal, so that it is forced to open a pager even if the output is just 5 lines.

Executing !/bin/sh while on a pager gives us root privileges.

–